Ensuring the high availability of operational data is an investment in business sustainability, development and security!
Advantages of backup and recovery solutions implemented by LIREX:
Comprehensive strategy
We will develop a comprehensive backup and recovery strategy tailored to your business needs.
Business continuity
Achieving business continuity is a priority for our experts.
Protection against financial losses
Data loss could be expensive. Protect your finances by implementing an advanced backup and recovery solution.
IT technologies and practices
Nowadays, with the evolvement of IT technologies and practices, ensuring data backup and recovery can turn into an investment directly increasing business resilience, development and cyber protection.
Backup, Archive and Recovery solutions, that are flexible and tailored to the organization’s objectives and the IT environment include integrated implementation of the two main backup types: backup of business data and backup of applications’ configuration. Thus, backups are not just a copy of data stored somewhere, but they add value to the organization. Both, the IT management and the organization as a whole, can benefit from them.


Some of the main benefits for the business are:
Increasing ROI (return on investment) – ensures both business continuity and the needed IT environment for business development
Flexibility
Improves flexibility and ability to a timely reaction in line with market trends
Audit efficiency
Making the external audit process faster and more efficient
Some of the main IT management benefits are:
spin-up
of development and testing environments before launching in production
sand-box
for DevOps purposes, training, problem analysis or compliance requirements
Data centre migrations
“physical” movement between on-prem and cloud environment
Workload migration
between physical and virtual platforms
According to Veeam’s 2022 survey results, as a result of crypto virus attacks, data center servers were encrypted in 48% of respondents, remote office platforms were encrypted in 49% of respondents and cloud servers were encrypted in 46% of respondents.
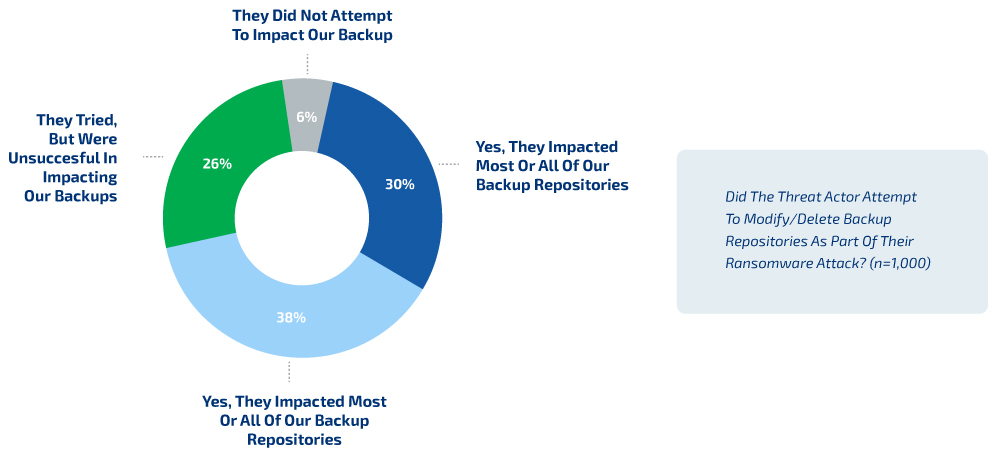
But actually, the most worrying is the trend of cyber criminals destroying organisations’ backups, as shown in the figure below.
In only 6% of the cases, cyber criminals did not attempt to impact backup data. In 38% of respondents, some backup repositories were impacted and 30% reported that most of their backups were impacted.
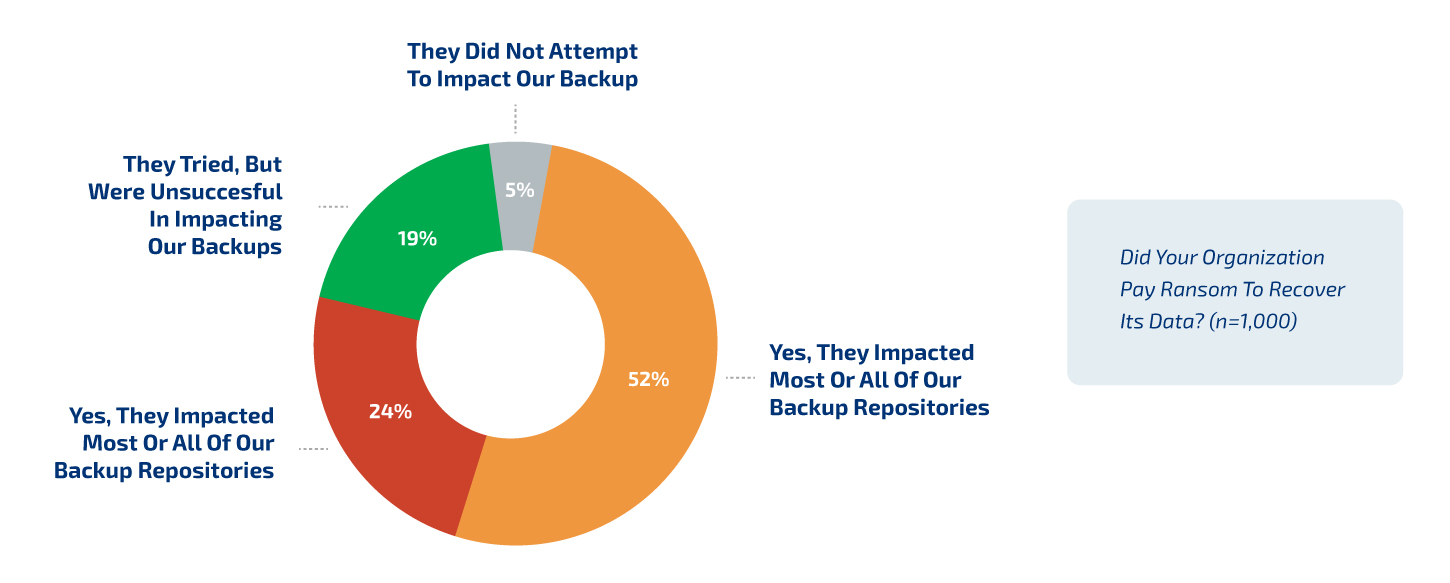
Another graph from the same report shows that there are many organisations that pay the ransom demanded but still do not have their data recovered – this is nearly ¼ of ramsomware victims. Only 5% of the impacted organizations did not have a ransom demanded after the attack, and just under 20% were able to recover their data without paying a ransom. Around half of those affected have paid the ransom and recovered their data. About half of those impacted paid the ransom and recovered their data.
Despite the global awareness of the threat of ransomware, for some organisations backups continue to be an underestimated area that is regarded only as a cost rather than a business resilience component.
Backup and recovery strategy
Operational data loss due to security breaches, technical failure or just a human error is a real threat that can cause huge damage to the organization. Therefore, the best practices recommend the 3-2-1 backup rule: 3 copies of the data, 2 copies on different storage media, and 1 offsite copy (at another physical location, another region, or another availability zone).
However, this alone is not enough. It is necessary to look at it from the point of the overall backup and recovery strategy which is the basis for achieving Business Continuity.
Furthermore, the business objectives defined within the strategy (recovery time and point objectives – RTO and RPO) align those management priorities and considerations with the IT. Regular testing of recovery procedures gives visibility on business objectives completion, as well as provides information about required resources. Regular testing is a key part, but still, it is often overlooked.
A strategy for achieving business continuity is needed even when all corporate data is in the cloud. In such a case, the responsibility for data protection lies within the service provider. Still, there is a question for you: How can you mitigate the risk of having all critical corporate data in the hands of an external provider(s)?
Are the technological measures for protection against equipment failure enough?
The provision of additional storage space for data copies, independent from a single external provider, is a technological measure for increasing data availability. In this way, you achieve a level of protection against technical malfunctions, and data loss caused by technical failure.
However, these measures alone are not enough to ensure business continuity in case of human or logical errors. Nor do they provide a direct benefit for business applications development, such as: providing an up-to-date environment for developing new services or for implementation of new systems; providing flexible platforms or service provider choice; avoiding vendor/technology lock-in.

Key technological factors in backup and recovery which are important for business development and cyber security:
Application aware backup
Granular data access during the restore
Applications and workload coverage for physical, virtual and cloud IT environments


 Български
Български