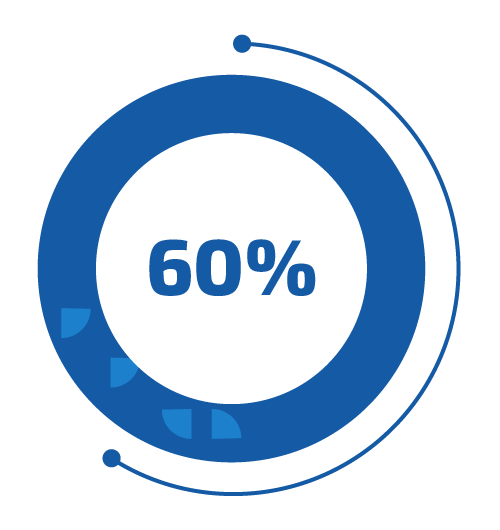
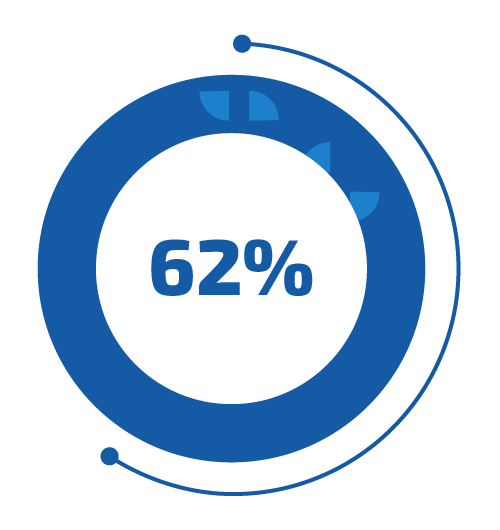
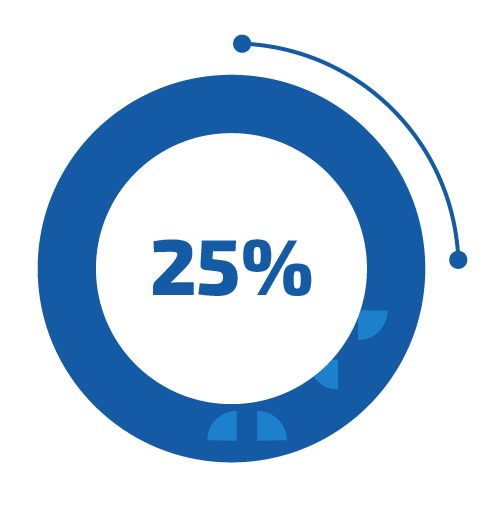
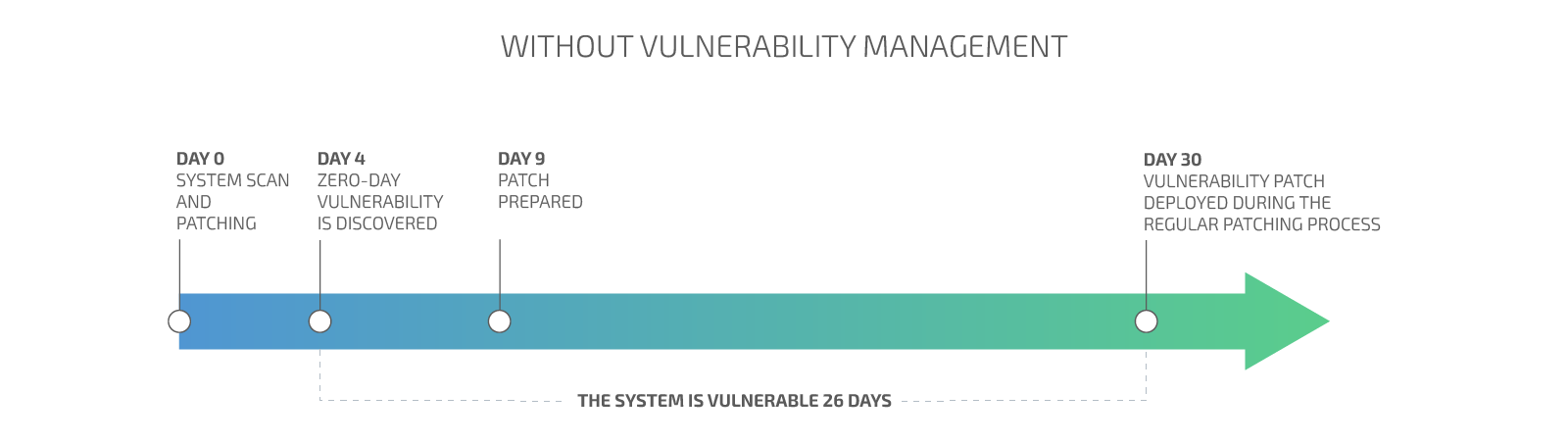
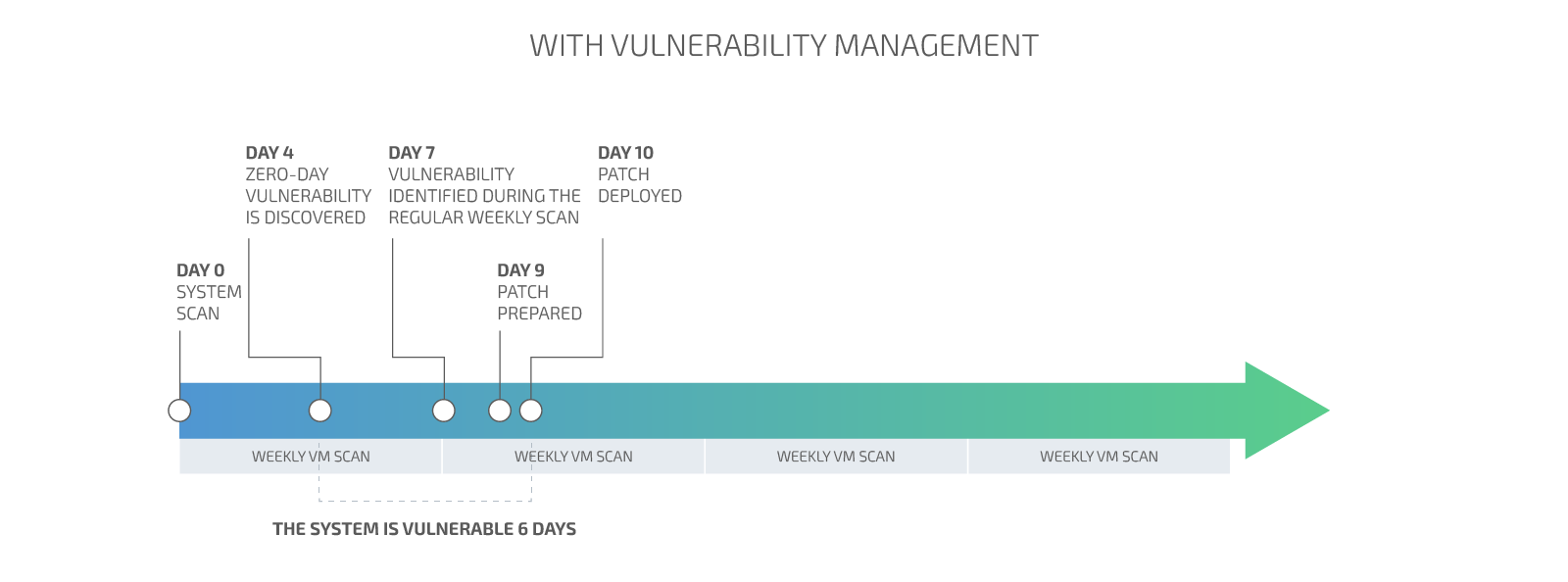
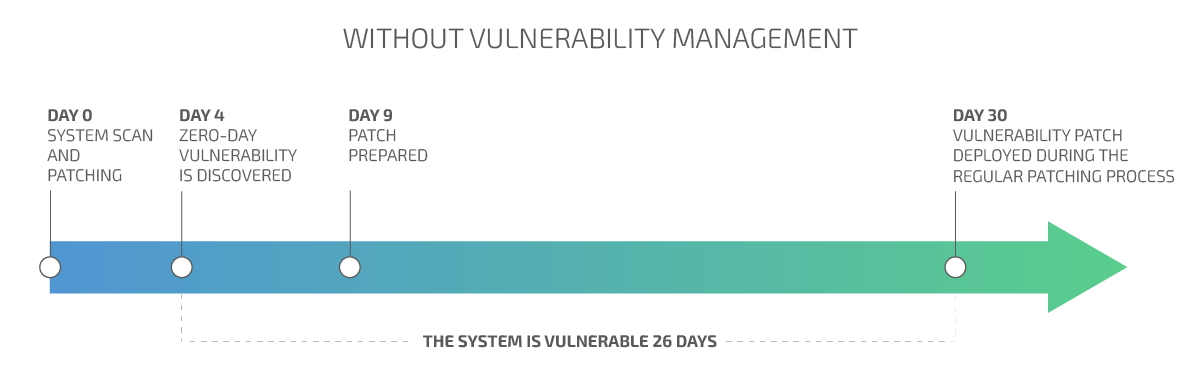
Minimize the security risk by decreasing the time for vulnerability remediation
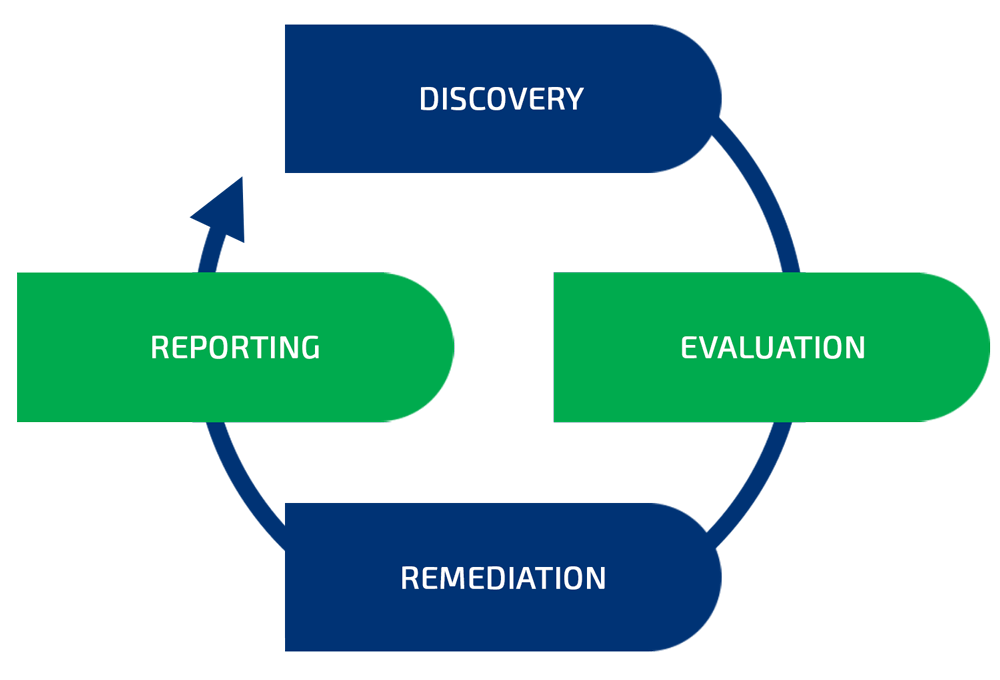
Prioritize the risks
The risk each vulnerability is posing to the organization is ranked and prioritized using automation tools as well as human expertise. The analysis takes into consideration each particular organization’s environment and business processes.
Decrease attack surface
Minimizing the time for vulnerabilities discovery and reactions decreases the attack surface and the overall risk exposure.
Improved tracking and control
Actionable information about the past trends and the current state in regards to vulnerability and risk.

 Български
Български