So much more than virus protection!
Mobility and Security
Meet the needs for mobility in today’s dynamic work environment without compromising corporate data security.
Increased productivity
Achieve higher productivity by providing secure and convenient corporate data access via various devices;
Complete protection
Protect user devices not only against malware and attacks but also in case of loss or theft.

End-point security is more than just protection against viruses. Modern security solutions not only provide protection against various types of malicious code and attacks but also bring additional benefits:
For the organization
gives the organization the confidence that endpoint devices are in line with the adopted security policies and data and applications’ risk is reduced
For the users
allow the user to use business applications seamlessly from any location and without worries about loss security issues
For the business
the end-user integrated security gives the business confidence in achieving higher productivity.
Compliance with organizational policies
In the corporate environment, the key to protecting the end-user is not only safeguarding the device from malware, phishing/spam and other attacks but also ensuring the enforcement of the adopted security controls by the organization:
ОS updates/patches to be installed and controlled
Installed applications must comply with the approved list, according to the user role or level
“Cyber hygiene” compliance in the use of applications and data exchange
Enablement of partial or complete device/user remote access restriction
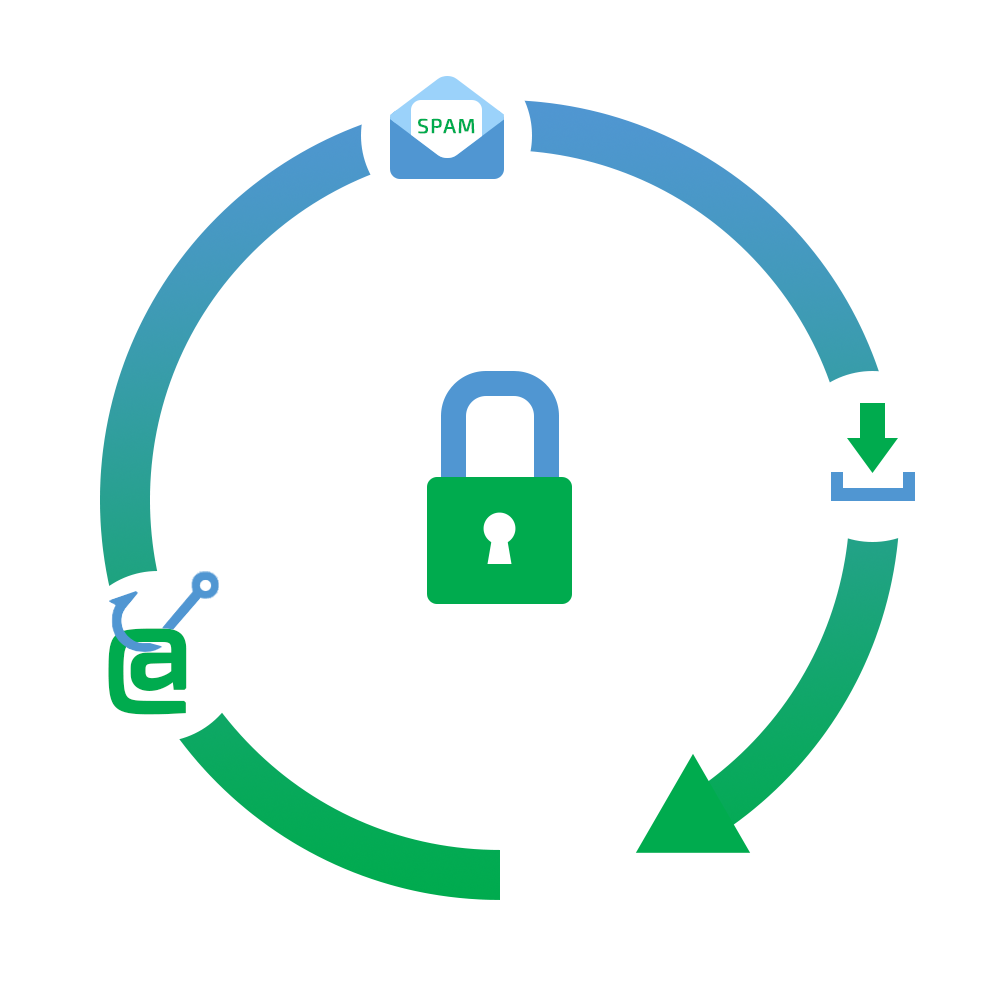
Protection against loss and theft
In addition to protecting the end-user from cyberattacks, it is advisable to consider protecting the devices in the event of loss or theft. In this scenario, their protection must also withstand unauthorized physical access by outsiders.
An example of such an additional measure, effective but often overlooked, is when closing your laptop the data and files become not accessible in a readable form before re-authentication.

Backup, sync and reminders
The risk of backdoor, crypto bots and keyloggers can be mitigated by endpoint protection solutions safeguarding against malware and other attacks. They can be locally installed, managed centrally, or used as a service.
However, the importance of backing up and synchronizing data, advising and alerting the user if the connection is secure or if they are sending email to external recipients is not so obvious as a measure, but also effective in addition to specialized security solutions.


Identity and Access Management и Single-Sign-On
Safeguard the corporate systems and Apps from unauthorized access

PRIVILEGED ACCESS MANAGEMENT (PAM)
Privileged Access Management (PAM) is at the heart of Zero trust policies

 Български
Български